| Uploader: | Sibiribiri |
| Date Added: | 08.08.2015 |
| File Size: | 69.40 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 47245 |
| Price: | Free* [*Free Regsitration Required] |
IKEv2 IPsec Virtual Private Networks (eBook) by graham bartlett, amjad inamdar (Author)
Download Full Ikev2 Ipsec Virtual Private Networks Book in PDF, EPUB, Mobi and All Ebook Format. You also can read online Ikev2 Ipsec Virtual Private Networks and write the review about the book. frameworks and protocols examined are IPsec, MOBIKE, SSL/TLS and SSH. Both IPsec and TLS/SSL Virtual Private Network, Host Identity Protocol, Mobile IP, MOBIKE, TLS/SSL, SSH, IPsec. IKEv2 – Internet Key Exchange Version 2 i-MIP – internal MIP IP – . Mar 14, · You’ll discover how IKEv2 improves on IKEv1, master key IKEv2 features, and learn how to apply them with Cisco FlexVPN. IKEv2 IPsec Virtual Private Networks offers practical design examples for many common scenarios, addressing IPv4 and IPv6, servers, clients, NAT, pre-shared keys, resiliency, overhead, and more.
Ikev2 ipsec virtual private networks pdf download
What's a VPN? Why do the need each other? Virtual Private Network VPN has become one of the most recognized terms in our industry, yet there continuously seems to be ikev2 ipsec virtual private networks pdf download impressions of what VPNs really are and can become, ikev2 ipsec virtual private networks pdf download.
Tiller Statement The authors explain each key concept, and then guide you through all facets of FlexVPN planning, deployment, migration, configuration, administration, troubleshooting, and optimization.
It provides the foundation necessary to understand the different components of Cisco IPsec implementation and how it can be successfully implemented in a variety of network topologies and markets service provider, enterprise, financial, government. This book views IPsec as an emerging requirement in most major vertical markets, explaining the need for increased information authentication, confidentiality, and non-repudiation for secure transmission of confidential data.
The book is written using a layered approach, starting with basic explanations of why IPsec was developed and the types of organizations relying on IPsec to secure data transmissions. The book covers the design and implementation of IPsec VPN architectures using an array of Cisco products, ikev2 ipsec virtual private networks pdf download, starting with basic concepts and proceeding to more advanced topics including high availability solutions and public key infrastructure PKI.
Sample topology diagrams and configuration examples are provided in each chapter to reinforce the fundamentals expressed in text and to assist readers in translating concepts into practical deployment scenarios. Additionally, comprehensive case studies are incorporated throughout to map topics to real-world solutions. Such connectivity is now vital to maintaining a competitive level of business productivity. Although several technologies exist that can enable interconnectivity among business sites, Internet-based virtual private networks VPNs have evolved as the most effective means to link corporate network resources to remote employees, offices, and mobile workers.
VPNs provide productivity enhancements, efficient and convenient remote access to network resources, site-to-site connectivity, a high level of security, and tremendous cost savings. Divided into three parts, the book provides a solid understanding of design and architectural issues of large-scale, secure VPN solutions.
Security titles from Cisco Press help networking professionals secure critical data and resources, prevent and mitigate network attacks, and build end-to-end self-defending networks.
Two leading authorities cover all facets of IPSec architecture, implementation, and deployment; review important technical advances since IPSec was first standardized; and present new case studies demonstrating end-to-end IPSec security. New coverage also includes in-depth guidance on policies, updates on IPSec enhancements for large-scale ikev2 ipsec virtual private networks pdf download environments, and much more. However, using the Internet to carry sensitive information can present serious privacy and security problems.
By explaining how VPNs actually work, networking expert Jon Snader shows software engineers and network administrators how to use tunneling, authentication, and encryption to create safe, effective VPNs for any environment.
Source code is available for download, and an appendix covers publicly available software that can be used to build tunnels and analyze traffic flow. Snader Statement The only book available that extensively covers the combination of VPN technology and Linux, this volume teaches first hand how to build various VPN solutions with individual setup guides.
VPN Protocols Explained - PPTP vs L2TP vs SSTP vs OpenVPN
, time: 6:27Ikev2 ipsec virtual private networks pdf download
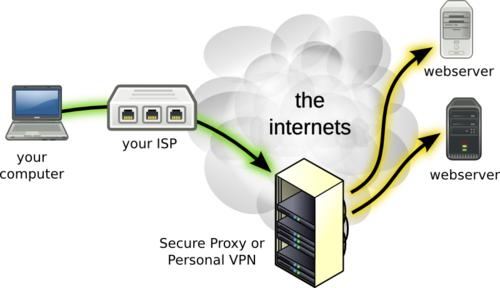
IKEv2 IPsec Virtual Private Networks Book Summary: Create and manage highly-secure Ipsec VPNs with IKEv2 and Cisco FlexVPN The IKEv2 protocol significantly improves VPN security, and Cisco’s FlexVPN offers a unified paradigm and command line interface for taking full advantage of it. Simple and modular, FlexVPN relies extensively on tunnel. Mar 14, · You’ll discover how IKEv2 improves on IKEv1, master key IKEv2 features, and learn how to apply them with Cisco FlexVPN. IKEv2 IPsec Virtual Private Networks offers practical design examples for many common scenarios, addressing IPv4 and IPv6, servers, clients, NAT, pre-shared keys, resiliency, overhead, and more. easy, you simply Klick IKEv2 IPsec Virtual Private Networks: Understanding and Deploying IKEv2, IPsec VPNs, and FlexVPN in Cisco IOS book download fuse on this page or you may relocated to the gratis subscription form after the free registration you will be able to download the book in 4 format.

No comments:
Post a Comment